One of the biggest challenges of internet companies is how they can accept payments online. We have already covered the major payment gateways that startups in the US, Europe, Australia, and Asia can use. However, some companies opt to store their customers’ credit data in-house. Why would you want to use an in-house database as your credit card vault? And is using a database to store credit card information safe?
Some startups like 37 Signals switched from using third-party payment processors to custom in-house systems. However, other companies have tried using in-house systems with disastrous consequences. Many times, headlines detail companies crippled by a breach of data security. Whether it is a large-scale attack or simply a case of an employee abusing access to sensitive cardholder information, the results can be devastating.
Cardholder data stored in a company’s database is exposed to a number of internal and external risks. Companies that fail to safeguard cardholder data not only lose their customers’ confidence but can also be slapped with heavy fines for being non-PCI compliant and face other legal problems.
And with 80% of customers preferring card payments over cash, it’s not an issue that’s going anywhere.
This article will outline the risks involved in storing credit card data yourself, as well as some helpful tips for managing credit card data safely.
Can A Merchant Store Credit Card Information?
The short answer here is yes.
The long answer is that there are certain things you can store and certain things you can’t, in order to be compliant and to ensure you’re treating your customers’ credit card details safely.
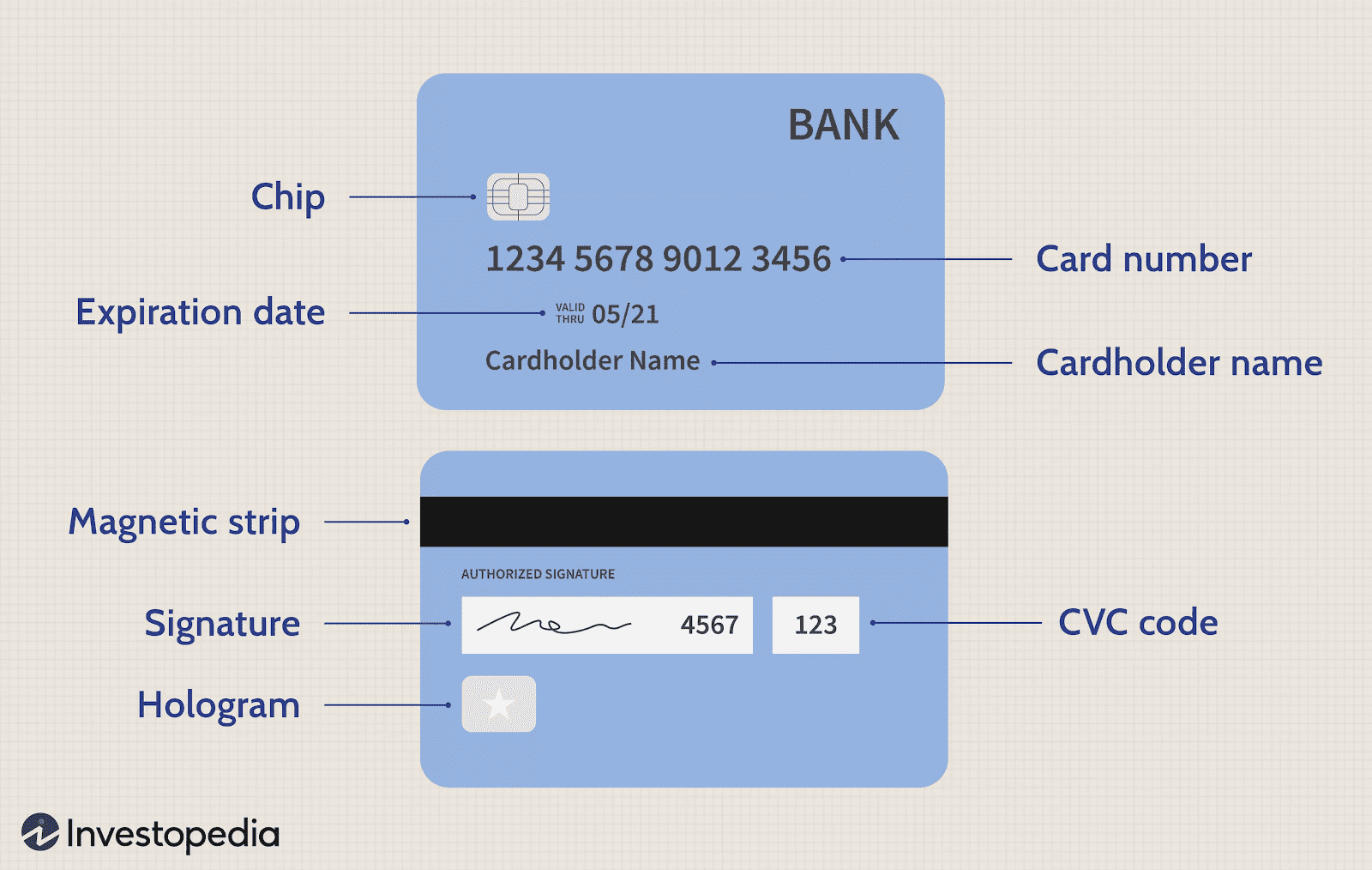
You also need to make sure your data is encrypted, and if it is, then merchants can store:
- Cardholder name
- PAN (Primary Account Number) (the 16-digit number on the front of the card)
- Expiration date
- Service code (You won’t find this data on the card itself. It lives within the magnetic stripe
Here’s what you can’t store, even if the data is encrypted:
- Sensitive authentication data (e.g., the full magnetic stripe info)
- PIN
- PIN block (i.e., the encrypted PIN)
- CVV/CVC (the three or four-digit code on the back of the card)
Knowing your responsibilities as a merchant is crucial, as the number of data breaches is increasing year on year, at rates as high as 54% annually.
The news is even worse for US vendors, being the most credit fraud-prone country. US card fraud losses make up over 38% of worldwide statistics.
5 Risks of Storing Credit Card Data in Databases
Databases have the highest rate of breaches among all business assets.
Hackers and malicious insiders target databases for one simple reason; it is where customer records and other confidential business data are stored. When malicious third parties access cardholder data, they can quickly extract value, impact business operations, or cause massive damage.
Many startups do not invest in database security as they should, with not much more than 50% of businesses meeting PCI DSS compliance guidelines.
The vulnerability of databases is ultimately based on its technology. Below are some reasons why you should not use your database as a credit card vault.
- Privilege Abuse
- SQL Injection & Malware
- Weak Audit Trail
- Storage Media Exposure
- Misconfigured Databases & Limited Security Expertise
Let’s go through them in detail.
1. Privilege Abuse
When employees are given more privileges than their job functions require, there’s always a risk that they might abuse them. For example, a customer success team member whose job function requires the ability to change customer contact information may take advantage of excess privileges and increase a customer’s account balance.
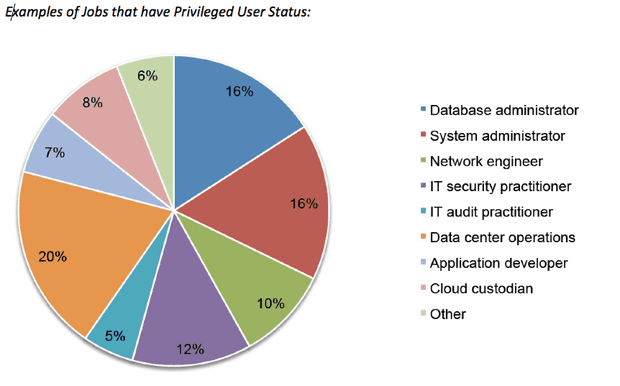
You might think you’re not at risk of this. After all, you’ve hired trustworthy staff, right? Well, that’s what everyone thinks, but a massive 74% of data breaches are because of abuse of privileges.
Despite there being a number of key roles that often involve privileged user status, only 48% of companies have a password vault and just 21% use multi-factor authentication for privileged access.
On the same note, companies often forget to revoke access to database privileges of employees who leave them. If the employees depart on bad terms, they can use their former privileges to inflict damage or steal high-value data.
Authorized users may abuse database privileges for unauthorized use. For example, an employee may be granted access to the database with certain limitations such as disabled printing and saving of electronic copies. However, these limitations can be circumvented by connecting the database with an alternative client such as Excel, enabling retrieval and printing of the data in the database.
2. SQL Injection & Malware
SQL injection is a code injection technique that hackers use, in which malicious SQL statements are inserted into an entry field.
SQL injections can provide data hackers with unrestricted access to databases. For SaaS companies, this is even dangerous, given that the injections can be deployed through a vulnerable web app or stored procedure. When the malicious statements are injected and executed, the data stored can be viewed, copied, or altered.
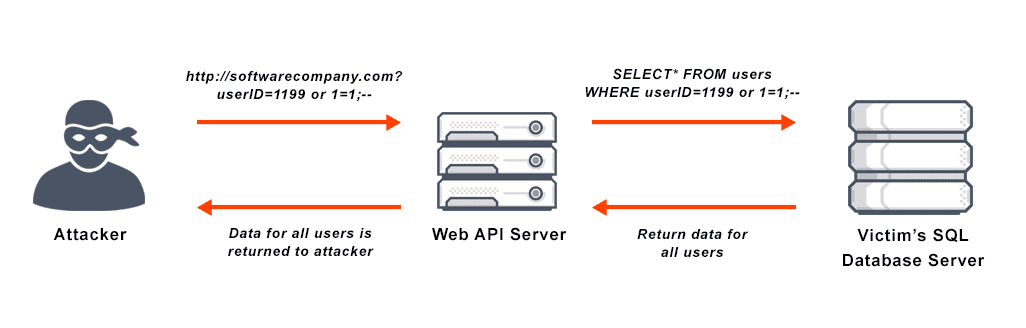
Though it might sound like the stuff of sci-fi hacker films, SQL injection attacks are pretty common. Hundreds of sites fall victim to these attacks every day. Imperva, a cybersecurity company, states that at least 80% of the websites they protect face an attempted attack each month.
Another common practice that compromises databases is the use of malware. These are usually used by spies, state-sponsored hackers, and cybercriminals and include spear-phishing emails sent to steal data. Usually, the malware will be deployed through a file and executed when an unaware user opens the file.
A common example of this is through spam emails. A hacker might send an email to one of your staff that appears to be related to their specific role. When they open it, the malware is automatically installed, and your data is infiltrated. To prevent this kind of fraudulent action, use the SPF checker.
3. Weak Audit Trail
Part of the database deployment should be the automated recording of transactions involving cardholder data. This is known as the audit trail.
Here’s what one might look like:
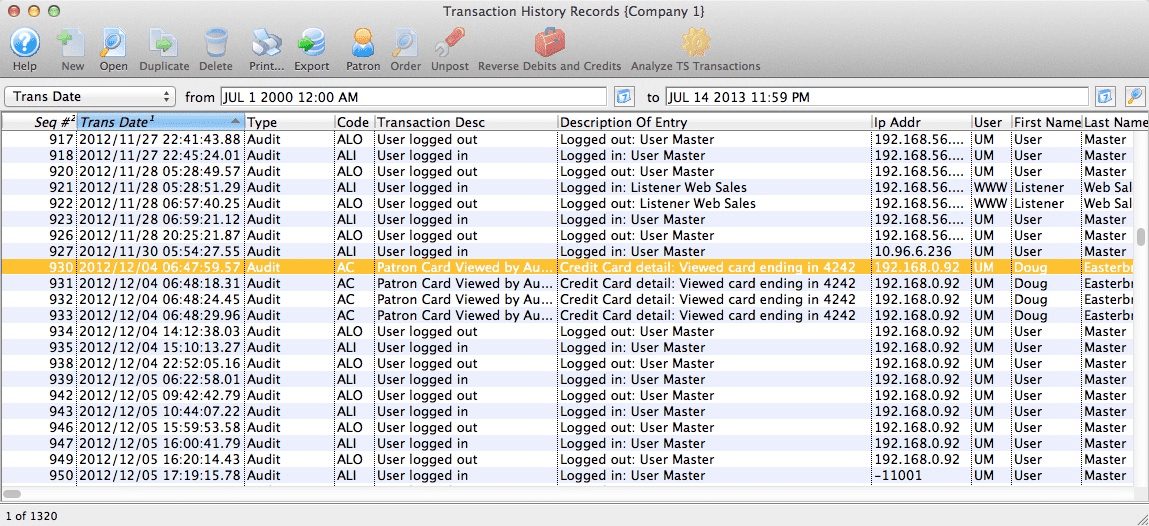
Failure to collect detailed audit records can be risky for your startup in many ways. For example, you may find your business on the wrong side of government and industry regulatory requirements.
That’s right, keeping audit logs is an important part of the PCI DSS requirements. Businesses must keep audit logs for at least one year, with ninety days of PCI audit logs being made available for immediate analysis.
Companies that accept credit card payments online are required to be PCI-compliant, and failure to be compliant can result in heavy fines. These fines can be as high as $100,000 every month until the company reaches compliance expectations.
So, it’s not something to be taken lightly.
4. Storage Media Exposure
Backing up your data is common practice, but it can also put your business at risk if you don’t do it securely, not least because your data is able to be attacked in more than one place.
We’re not talking about someone breaking into your office in the middle of the night and making off with your hard drives, though there are many cases where security breaches have involved the theft of database backup tapes and disks.
We’re talking about online storage backups.
A massive 2.3 billion files are exposed across online file storage tech, as a result of businesses not taking their backups seriously.
Any data that is stored in a backup storage media is often completely exposed to an attack. This is often avoidable by choosing a storage provider with strict security measures and data encryption procedures.
Before you start backing up your data, it’s important to find a secure online platform where you can handle all sensitive information and transactions. Nowadays, companies will use virtual data rooms to store, share, and work on high-priority data and sensitive documents that must not get leaked into the public domain. It’s important to have such a safe cloud platform in order to eliminate the risk of data theft.
After you have a secure data room, you can then go ahead and create separate data backups and restore point
5. Misconfigured Databases & Limited Security Expertise
Here’s a concerning statistic: 54% of companies are only ‘somewhat confident’ that they’d be able to spot a data security breach in time to do anything about it.
Clearly, many business owners have fairly limited security expertise when it comes to storing credit card information. As a result, it is common to find databases that still have default configurations and accounts.
Attackers know how to exploit these vulnerabilities to get data from the databases. Most organizations do not patch their databases with the latest security upgrades in time. In most cases, it takes several months for a database to be patched, especially if it contains enormous data, and the patch may lead to some downtime. During the period that the database remains unpatched, attackers can launch attacks.
The online security environment is constantly evolving, and service providers strive to stay ahead of hackers. However, the internal security controls at most businesses are not keeping pace with data growth and security technologies. Most companies are ill-equipped to deal with a security breach. This is often due to the lack of expertise required to implement training, policies, and security controls.
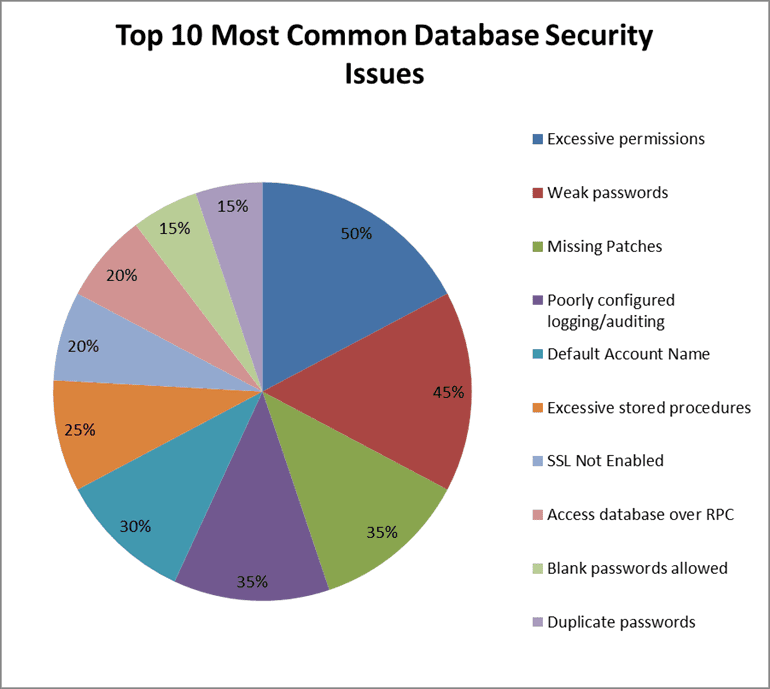
Again, lack of expertise is a huge contributor to data breaches, with 36% of error-related breaches having something to do with a database misconfiguration.
How Do You Securely Collect Credit Card Information?
So, you know the risk involved with improper storage of credit card information. You’re sufficiently motivated (or is it scared) by the potential fines and downtime that your business could suffer if you don’t get it right, but you desperately need to offer credit card as a payment option.
After all, it’s how everyone wants to pay now.
You know that credit card fraud makes up 35% of all identity theft cases, and you don’t want a security breach on your company’s part to contribute to that statistic.
How then do you go about storing credit card information safely?
Let’s take a look at the ten dos and don’ts of storing credit card information.
1. DO: Question if storing credit card data is really necessary
There are a number of instances where you might not actually need to keep this information. For example, if the majority of your buyers are one-off or infrequent customers (such as many e-commerce stores), then you might not need to hold onto it at all.
If you’re a SaaS company with recurring billing though, or your customers purchase from you regularly, then you might have a case for storing credit card information.
2. DO: Make sure you know what the PCI standards are
Being well-informed is your best starting point in your defense against credit card data theft.
Make sure you know the risks involved in getting a PCI fine, which can be hundreds of thousands of dollars.
Also, bear in mind that if your company operates across multiple locations, they’re all responsible for maintaining PCI standards.
3. DON’T: Write down and credit card numbers
Make sure all of your employees understand the risks involved here. If you ever need to take credit card details remotely, do so through a secure payment gateway.
If you’re processing a single payment on a manual machine, get the details over the phone and plug them straight in. Don’t write them down, and don’t ask for them over email.
4. DON’T: Use the regular text field to capture card details
Regular text fields are highly vulnerable to outside threats. Make sure to always use an official payment gateway for capturing credit card numbers online.
5. DO: Handle PCI responsibilities with a robust system
A good system backbone to follow (and one backed by the PCI Security Council) is this: Program, Policy, and Procedures.
Your program consists of strategic objectives, individual roles and responsibilities, and your overall plan to achieve those business objectives.
From there, you’ll develop a policy, which typically includes a statement of intent or a list of rules that must be followed. Examples include how often to change passwords, who has access to which privileges, etc.
Your procedures take things to the next level of detail, outlining step-by-step tasks that employees must follow. The importance of having well-documented procedures is paramount, so you should ensure they are easily accessible and become part of the onboarding process for all applicable team members.
6. DON’T: Use your CRM as a vault for credit card information
I know, we all want everything in one place.
This simply isn’t a risk worth taking, with 35% of US consumers having fallen victim to credit card fraud.
Your CRM isn’t the place to store credit card data, as it doesn’t have the level of security required to be PCI compliant.
7. DO: Have your customers sign an agreement
If you are going to store customer credit card details, make sure you get a signed agreement in place first.
This will help to mitigate risk and ensure that they actually know what you’re doing with their data.
8. DO: Check for updates regularly (hardware and software)
Before you start collecting and storing credit card information, make sure you have a robust system in place for routine hardware and software checks.
It’s no lie that technology is advancing at a rapid pace, and when it comes to data security, there is an ongoing battle between the makers of security software and hardware and the hackers that seek to steal your data.
If you aren’t updating both regularly, you could easily find yourself falling behind in that race, leaving your customers’ information seriously vulnerable.
9. DO: Exercise caution when remotely accessing work systems
With many of us regularly working from home, be it full time, or be it an hour or two catching up in the evening, there’s an additional risk posed.
That’s because your home network is likely to be much less secure than your work network. It’s worth putting a procedure in place for employees working remotely, as well as asking the question: can this wait until tomorrow?
10. DO: Choose a compliant payment processor
The best way to protect your company data and make sure you’re adhering to PCI compliance regulations is to work with a competent payment processor like Stripe.
You’ll also know that they’re doing the right thing, regularly updating their own hardware and software to ensure maximum data safety.
Key Findings
The cost of keeping credit card data safe is enormous for any starting company. Developing your own billing system can delay your launch date by months and significantly increase your costs. Moreover, there are many robust third-party online gateways that will fit your requirements.
We already covered the pros and cons of building vs. buying an existing payment billing system.
When choosing a billing system, there are a couple of things you should consider. The most important one is whether the service provider is PCI-compliant. Apart from this, you can look at other factors such as transaction charges, set up and related transaction fees, ability to customize the checkout pages, among others.
Most third-party gateway systems will enable you to start receiving payments within a few hours to a few days. In fact, some providers only require you to add a line of code on your pages to integrate their payment gateway.
Looking for a robust subscription revenue infrastructure that’s PCI-compliant?