Being an eCommerce merchant, how prepared are you to deal with the expense of lost products and their shipping charges, chargeback fees, your brand image taking a hit, and the probable loss of your account?
Online transactions entail the transfer and storage of personal information (financial information, authentication information, passwords, etc), and the misuse of this information leads to a host of frauds and scams, credit card fraud being one of the major threats. This can further catapult into crimes like identity theft.
Card-not-present (physical card not present during a transaction) fraud losses are projected to increase from $5.3 billion in 2017 to $7.2 billion in 2020 (source: Aite Group). The consequences of this loss affect not only the goliaths of the world like Walmart or Tesco, but have a greater negative impact on smaller businesses.
According to ACFE’s 2016 report, “The median loss suffered by small organizations (those with fewer than 100 employees) was the same as that incurred by the largest organizations (those with more than 10,000 employees). However, this type of loss is likely to have a much greater impact on smaller organizations.”
So how can small businesses safeguard themselves from this threat?
Sarah Grayson from the web security team at McAfee believes, “One of the best ways to keep your business safe from cybercriminals is layering your security. Start with firewalls, an essential aspect in stopping attackers before they can breach your network and gain access to your critical personal information. Add extra layers of security to the website and applications such as contact forms, login boxes and search queries. This will ensure that your eCommerce environment is protected from application-level attacks like SQL (Structured Query Language) injections and cross-site scripting (XSS).”
One such security layer is your payment gateway, which ensures that there are no vulnerabilities present when you are processing payments, thanks to its credit card fraud detection techniques and tools.
This post will take a stab at explaining what credit card fraud can do to your business, and how your payment gateway can provide you with anti-fraud tools to detect and prevent online card fraud. But first, let’s start with what credit card fraud looks like. In case you want to jump to the list of fraud prevention tools you absolutely need to have, click here.
What is a Credit Card Fraud?
Starting with the basics, a credit card fraud takes place when a cardholder’s credit card is lost or stolen, or the cardholder’s personal information (credit card number or pin) is used to make unauthorized transactions.
Even to process such transactions, businesses have to pay interchange rates, assessment fees, and markup fees, along with facing other consequences like:
- Lost Revenue and Resources: You will have to bear the cost of shipping in addition to losing the merchandise when an online payment is made for these transactions. If you choose to verify suspicious transactions by contacting the corresponding customers with an internal or an external team, that will also add to your cost, time, and effort.
- Chargeback: You will have to pay a particular fee to the bank for every disputed or fraudulent transaction.
- Possible termination of your account: When the percentage of chargebacks exceeds the processed revenue by a certain value for several consecutive months, then you might lose your merchant account. Usually, card networks expect merchants to keep their chargebacks rates between 1%-2%.
To avoid these consequences, you need a system in place to detect and prevent fraudulent transactions from taking place.
Security Tools for Credit Card Fraud Detection
The key is to adopt a payment gateway that employs a mix of the most effective techniques to tackle credit card payment fraud, minimize losses, and safeguard your business from the aforementioned threats.
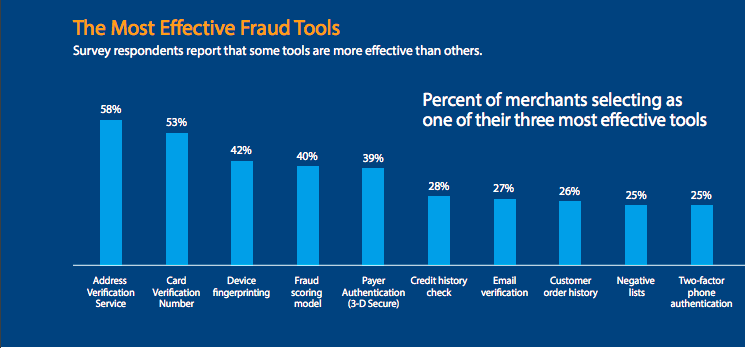
Image Source: CyberSource
Let’s look at the major fraud tools in detail:
Verification
Mentioned below are some security tools that help you as merchants, to gauge the authenticity of the user, by matching the information entered with what is present in the database of the customer, bank, or industry. Transactions that fail these tests can be flagged or blocked, based on the pre-defined payment gateway settings.
Enable an Address Verification Service (AVS) Filter
Address verification is conducted by comparing the billing address and zip code from a transaction with the details on file at the issuing bank. The AVS responds with a code that will help you understand if both the billing address and zip code match (full AVS match), either one of them matches (partial AVS match), or neither of the two match (no match). When there isn’t a full AVS match, the bank will flag the transaction. In such cases, you can either investigate further by checking the CVV (Card Verification Value), email address, and IP address, or simply allow your payment gateway to decline the transaction.
Capture Card Verification Value (CVV) Codes
The CVV (or Card Verification Code) is a 3 or 4-digit code that is printed on the back of every credit or debit card, which should not be stored in the merchant’s database for any kind of transaction.
While processing a card-not-present (CNP) transaction (online, email, or telephone orders), you get the required card information from the customer for verification. If the CVV codes do not match, you should allow your payment gateway to decline the transaction. Though this won’t completely eliminate online card fraud, you will be minimizing your risk of facing chargebacks.
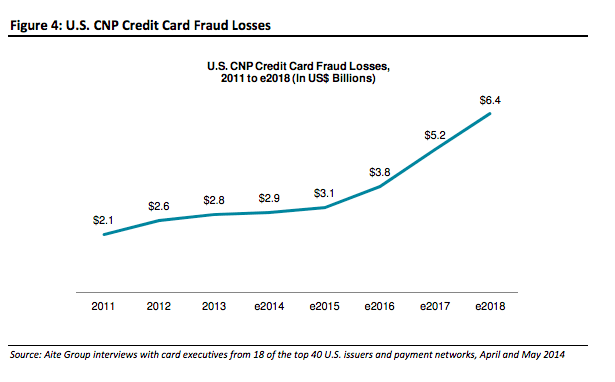
Image Source: Aite Research
Screen with Device Identification
Device identification analyzes the computer rather than the person who is visiting your website. It profiles the operating system, internet connection, and the browser, to gauge if the transaction has to be approved, flagged, or declined. All devices (phones, computers, tablets, etc) have a unique device fingerprint (similar to human fingerprints) that helps identify fraudulent transaction patterns and assess risks, if any.
Companies like ThreatMatrix monitor the device ID, using it as a reference point to see if other people have flagged it for suspicious or fraudulent transactions or activities in the past. Fraudsters cannot impersonate a computer’s unique identity, making it a great option to protect your business against online fraud.
Create Blacklists
Blacklists or fraud prevention blacklists contains all order details like credit card information, customer names, email addresses, physical addresses, and at times even countries that companies have identified as fraudulent or risky.
You will have to closely monitor orders made from countries considered to be “high-risk”. According to the Online Fraud Guide, some of the countries with the highest online fraud rates are Israel, Malaysia, Egypt, Pakistan, Ukraine, Russia, Bulgaria, Romania, Lithuania, Nigeria, and Yugoslavia. Before you ship items to these countries, exercise greater restriction by flagging the respective orders for further review and process them only when those customers verify their identities.
Blacklists are limited by nature, as fraudsters constantly change their details when they place an order online. So if you add customers to this list when they fail a security filter, you might sometimes end up blocking legitimate transactions.
Monitoring Anomalies
The following security tools help in identifying transactions which don’t meet certain set rules, and hold the possibility of being fraudulent. Depending on your payment gateway’s default and customizable settings, such transactions get flagged or blocked.
Flag Large Transactions
With stolen card information, fraudsters will generally take a shot at making large transactions before the card gets blocked. This will be detrimental to your business (big or small), where you will have to bear the cost of allowing this to take place. It might even lead to a payment gateway terminating your processing account.
You can limit large transactions by specifying a flat dollar amount (maximum amount for a transaction), to avoid chargebacks. In addition to this, you can limit the number of failed transactions from a customer that go through your payment gateway.
Conduct Velocity Checks
A velocity attack is when fraudsters use a software to generate hundreds of card number sequences, and run them on your website until a valid card number is found. Having a velocity check by defining a threshold for how many transaction attempts a customer has, will help identify such high-speed attacks. Apart from this, you also have the lockout mechanism, which is a type of fraud prevention measure meant to block fraudsters who use automatic card number generator programs. It works by blocking out transactions from a particular IP address with a large number of credit card transactions declined within a set time.
User Authentication
Having an additional layer of security to verify the identity of the user and confirm if they are who they claim to be for online credit card transactions, will strengthen your case for credit card fraud detection and prevention.
Secure Online Transactions with Payer Authentication (3-D Secure)
Payer authentication, referred as Verified by Visa (VeB) for Visa cards and SecureCode for Master cards, is a cardholder authentication measure that secures online transactions for customers. This allows them to create a PIN (secure code) that can be used during checkout to confirm the user’s identity. If the PIN entered is wrong, the transaction gets blocked, thereby reducing the number of transactions that have to be manually reviewed by you (as a merchant).
By implementing this, you will achieve chargeback protection and lower interchange rates, making it one of the most sought-after fraud prevention tools.
Evaluate with Risk Scoring
This tool uses machine learning methods to look at the various components of an online credit card transaction to determine the probability of it being fraudulent. You will need to evaluate the results of their transaction verification tools like AVS, CVV, device ID, etc. along with what the user is buying and where the user wants the item shipped. (Source:Burlington Bank Card). The higher the fraud score, the more the reason for you to decline the transaction.
Risk scoring will provide a case-by-case evaluation and will flag transactions based on the rules you choose, such as an AVS failure test, IP range, use of anonymous email addresses, billing address verification, and others. Predictive machine learning algorithms can learn from prior data and estimate the probability of a fraudulent credit card transaction.
What next?
To protect your business from card frauds and related losses, integrate with a payment gateway that has built-in fraud prevention tools. This way, you will have to manually review only the flagged transactions and will have much lesser at stake.
But in a lot of cases, implementing security measures that are not flexible leads to a large volume of legitimate transactions being declined on the grounds of suspected fraud. These false positives will discourage these customers to buy from you again. To save yourself from unnecessary trouble, you can make use of biometric authorization (fingerprint scanning, voice or facial recognition, digital signatures) or two-factor authentication (two-step verification) for cardholders to prove their identity. Where card readers are concerned, using EMV chip reader is highly recommended as the data encrypted on EMV chips is constantly changing and highly impossible to replicate.
Looking at it from a realistic standpoint, you have to venture beyond equipping your business with only a few security tools, and at the same time add flexibility for approving transactions.

